Mission control.
Intelligent surveillance.
Advanced drone fleet management with real‑time AI threat detection, autonomous patrol missions, and comprehensive analytics. Built for security, infrastructure monitoring, and critical asset protection.
How it works
From mission planning to verifiable reports — safely, consistently, and fast.
Mission Planning & Fleet Control
Coordinate multiple drones with automated patrol routes, geofencing, and real‑time fleet status monitoring across 12+ active units.
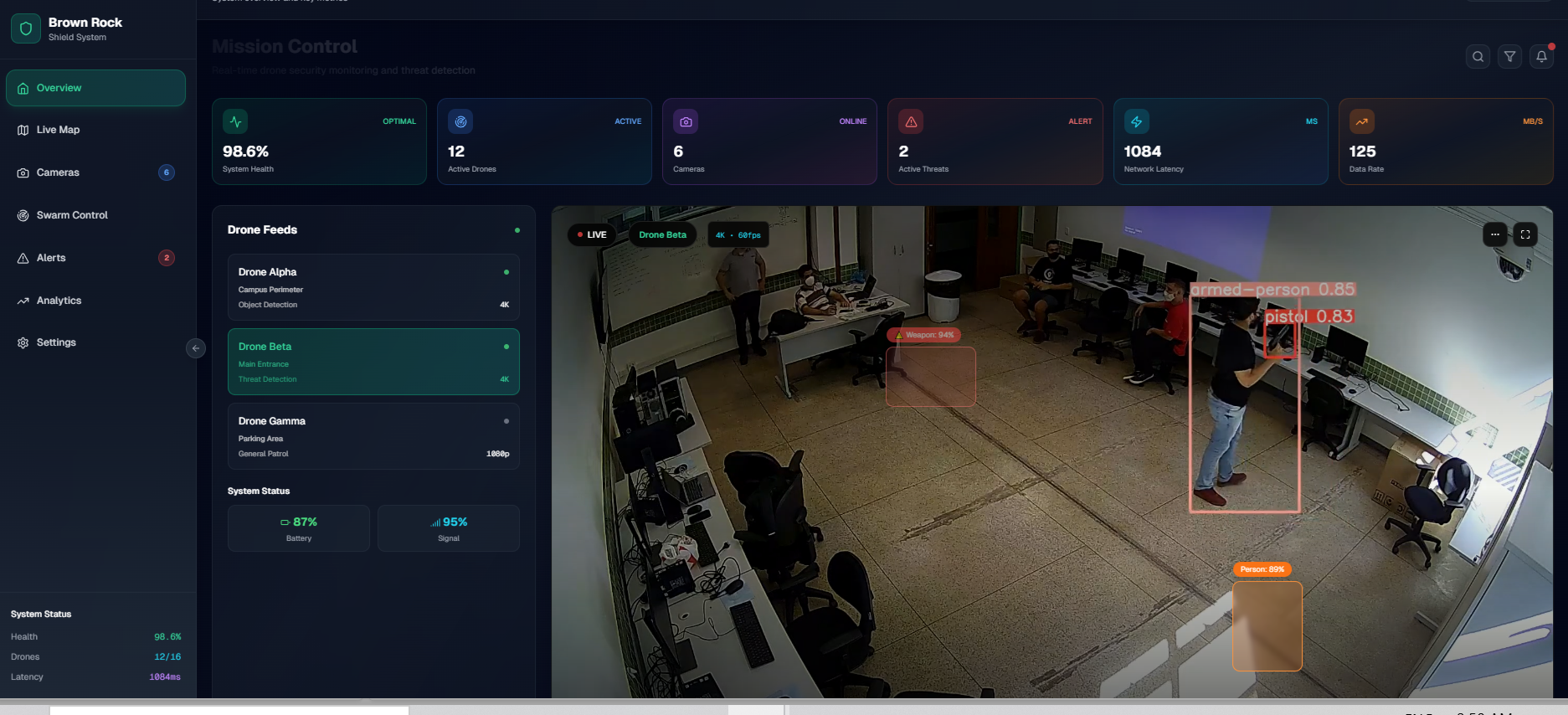
AI‑Powered Surveillance
Real‑time object detection and threat classification with confidence scoring. Identifies weapons, unauthorized personnel, and security breaches instantly.
Intelligent Analytics
Advanced computer vision processes live feeds with 98.6% system reliability, detecting threats with 85%+ accuracy and sub‑second response times.
Enterprise Security
Military‑grade encryption, audit trails, and compliance logging. Full chain‑of‑custody for evidence and incident documentation.
What it solves
High‑impact, measurable outcomes from day one.
98.6% system uptime
Enterprise‑grade reliability with redundant failsafes and automatic recovery.
Real‑time threat detection
AI identifies weapons, intrusions, and anomalies with 85%+ confidence in milliseconds.
12+ drone coordination
Simultaneous fleet management with intelligent task distribution and collision avoidance.
Multi‑site coverage
Centralized command center managing distributed security operations across facilities.
Military‑grade security
Encrypted communications, secure data handling, and compliance‑ready audit trails.
Live situational awareness
Real‑time mapping, threat visualization, and automated incident response coordination.
Simulated solar inspection
Replay a real mission with detections, GPS tracks, and thermal overlays. No signup needed.
Tip: Toggle thermal/RGB, open a detection to see coordinates and recommended action.

Live Threat Detection Demo
Experience real-time AI threat detection with confidence scoring and automated response protocols.
System Status
Camera Feeds
Detection Stats
Controls
Click "Start Gun Detection" to begin live demo
Real-time AI threat detection with confidence scoring
Fleet Status
Recent Detections
Architecture at a glance
Modular components that fit your ops and compliance.
FAQ
Can we operate fully autonomously?
Yes. Missions are pre‑planned with geofences and failsafes. Operators can intervene or run supervised autonomy per your policy.
Do you support thermal payloads?
Yes. We support RGB and thermal streams, synchronized capture, and CV models trained on your data.
How does blockchain fit in?
Each mission’s key artifacts (routes, detections, operator actions) are hashed and recorded to provide tamper‑evident audit trails.
Deployment options?
Edge, on‑prem, or private cloud. Network isolation, RBAC, and data retention policies are configurable.
Ready to launch your fleet?
Start a pilot across one or more sites — with your routes, policies, and reporting needs.